Attainable Security Elevated: Discovering HPE’s Gen11 Servers with iLO 6
Breaking Analysis: How HPE is Leading the Industry in Supply Chain Security
The state of the supply chain and the ability of the United States to secure it is being tested like never before in 2020. While the US has been increasingly relying on global supply, and offshoring the manufacture of many of the goods critical to our national security, the looming threat of counterfeit hardware, supply chain hacks by nation states, trade wars, and the disruption of entire industries during the COVID-19 global pandemic has brought sharp focus to the risks inherent with the status quo. Public sector agencies, financial services, healthcare, and other organizations requiring high security products are all reevaluating their reliance on globally sourced products for critical infrastructure. Leadership in the area of supply chain security is desperately needed.
Today, InfusionPoints is unveiling breaking analysis on HPE's new Trusted Supply Chain Initiative.
The Evolution of Server Security
In the fast-paced and interconnected digital landscape of today, where data breaches and cyber threats loom large, the significance of robust server security cannot be overstated. As organizations strive to protect their sensitive information and maintain the trust of their customers, the choice of server infrastructure plays a crucial role in safeguarding critical data and ensuring uninterrupted operations. HPE (Hewlett Packard Enterprise) has consistently prioritized server security, ensuring it remains at the forefront of their server development initiatives. With a steadfast commitment to protecting sensitive data and mitigating cybersecurity risks, HPE has dedicated substantial resources to implement cutting-edge security features like Silicone Root of Trust, Firmware Validation, iDevID, Platform Certificates and robust security management solutions across each Generation of Server Technology. By proactively addressing evolving threats, collaborating with industry experts, and leveraging their extensive expertise, HPE has established itself as a trusted leader in providing secure server infrastructure that meets the stringent demands of modern organizations.
Empowering Security and Management
HPE has revolutionized server security by introducing the iLO6 Security Dashboard, a simplistic and user-friendly tool that streamlines the process of implementing robust security measures. With a comprehensive checklist of security hardening best practices, the iLO6 Security Dashboard empowers administrators to effortlessly fortify their server infrastructure against potential threats.
By providing an intuitive interface and step-by-step guidance, the iLO6 Security Dashboard enables administrators to easily identify and address non-hardened configurations, ensuring that critical security measures are properly implemented. This innovative solution not only saves valuable time and resources but also enhances the overall security posture of HPE servers.
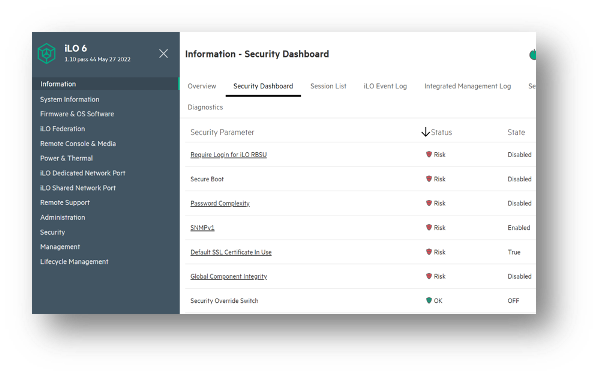
The iLO6 Security Dashboard equips administrators with a centralized platform to monitor and manage security settings, empowering them to stay one step ahead of potential vulnerabilities. With real-time insights, administrators can proactively detect and remediate security gaps, bolstering the defense mechanisms of their server environment.
By making server security accessible and user-friendly, HPE has transformed the landscape of server management, allowing organizations to confidently protect their valuable data and infrastructure. With the iLO6 Security Dashboard, HPE has simplified the implementation of security hardening best practices, empowering administrators to reinforce their server environment with ease and efficiency.
Security at Scale
While securing individual servers is crucial, many organizations encounter challenges when it comes to securing servers at scale. Recognizing this common pain point, HPE has introduced GreenLake for Computer Ops Management , a game-changing solution that empowers administrators to implement consistent security features across all systems swiftly and efficiently.
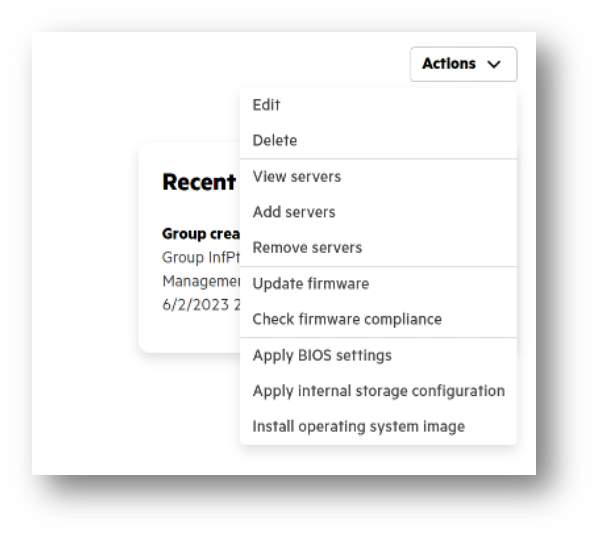
With HPE Greenlake for Compute Ops Management, administrators gain the ability to apply standardized security measures seamlessly across their server infrastructure. This unified approach ensures that every system is protected using the same robust security features, eliminating potential vulnerabilities that may arise from inconsistent or ad-hoc security practices.
By streamlining the deployment of security features at scale, HPE Greenlake for Compute Ops Management simplifies the management process and significantly reduces the time and effort required to secure a large number of servers. Administrators can efficiently roll out security configurations, updates, and patches simultaneously, ensuring consistent protection across their entire server fleet.
Scale, Automate, Secure
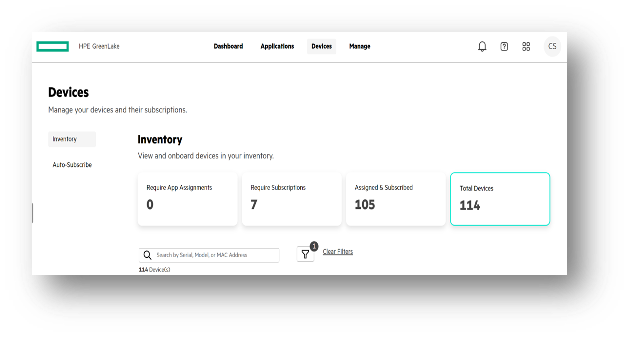
HPE has revolutionized server management at a scalable level with the introduction of HPE Greenlake for Compute Ops Management. This innovative solution empowers organizations to manage their servers efficiently and effectively, regardless of the scale or complexity of their infrastructure.
HPE Greenlake for Compute Ops Management provides administrators with centralized control and automation, enabling them to streamline server management tasks such as firmware validation, updates and enforcing compliance profiles to an organizations fleet. By leveraging this powerful tool, organizations can easily deploy, monitor, and maintain their servers, optimizing resource allocation and reducing operational overhead.
In addition to its scalable management capabilities, HPE has further enhanced the flexibility and integration through the adoption of the industry-standard Redfish API. This API facilitates seamless integration with Security Orchestration, Automation, and Response (SOAR) platforms, unlocking advanced automation and incident response capabilities.
HPE also allows customers to leverage the Security Protocol and Data Model (SPDM) to validate components within the system, ensuring a secure and trusted computing environment. By integrating SPDM, HPE enables comprehensive validation and attestation of system components, ensuring their authenticity and integrity. This enhanced security layer, coupled with the industry-standard Redfish API, empowers Security Orchestration, Automation, and Response (SOAR) tooling to rapidly act against machines that fall outside compliance. The combination of SPDM and Redfish API enables organizations to proactively identify and address security gaps, swiftly responding to potential threats and maintaining a robust security posture across their infrastructure. HPE's strategic utilization of SPDM and integration with Redfish API showcases their commitment to delivering innovative security solutions that provide real-time visibility, rapid response, and heightened protection in today's dynamic threat landscape.
By embracing the Redfish API, HPE enables organizations to integrate their server management with existing SOAR platforms, enhancing their security operations and incident management workflows. This integration empowers administrators to automate routine tasks, orchestrate complex processes, and respond swiftly to security incidents, significantly improving overall efficiency and resilience.
With HPE Greenlake for Compute Ops Management and the adoption of the Redfish API, HPE enables organizations to achieve streamlined, scalable server management while embracing advanced automation and SOAR capabilities. This comprehensive approach empowers organizations to optimize their server infrastructure, enhance security operations, and drive efficiency in managing their systems at any scale.
Conclusion
In conclusion, HPE's unwavering commitment to increasing server security, adopting industry standards, and prioritizing ease of use, including their powerful GreenLake for Compute Ops management solution for managing large and complex environments, sets them apart from competitors without compromising on advanced security features.
HPE understands the critical importance of robust security measures in today's threat landscape. By seamlessly integrating advanced security features into their user-friendly solutions, such as GreenLake for Compute Ops, HPE ensures that organizations can effectively protect their infrastructure without sacrificing ease of use. This unique approach enables customers to achieve comprehensive security, streamline operations, and confidently manage their complex environments, all while benefiting from HPE's cutting-edge security technologies and industry-leading standards compliance.
With HPE, organizations can experience the best of both worlds: advanced security features and intuitive management capabilities that together offer unmatched protection, simplicity, and peace of mind.
About InfusionPoints
InfusionPoints is your independent trusted partner dedicated to assisting you in building your secure and compliant business solutions, testing your security controls and defending your consumer, employee, and supply chain information.
Important Facts about this Paper
PUBLISHER: InfusionPoints, LLC
INQUIRIES: Contact us if you would like to discuss this report, and InfusionPoints will respond promptly.
-
+1-336-990-0252
CITATIONS: This paper can be cited by accredited press and analysts but must be cited in-context, displaying author “InfusionPoints, LLC”. Non-press and non-analysts must request prior written permission by InfusionPoints, LLC for any citations.
LICENSING: This document, including any supporting materials, is owned by InfusionPoints, LLC. This publication may not be reproduced, distributed, or shared in any form without prior written permission from InfusionPoints, LLC.
DISCLOSURES: This paper was commissioned by Hewlett Packard Enterprise (HPE). InfusionPoints provides security research, analysis, advising, consulting, and penetration testing to many high-tech companies in this space.
DISCLAIMER: The information presented in this document is for informational purposes only and may contain technical inaccuracies, omissions, and typographical errors. InfusionPoints, LLC disclaims all warranties as to the accuracy, completeness, or adequacy of such information and shall have no liability for errors, omissions, or inadequacies in such information. This document consists of the opinions of InfusionPoints, LLC and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice.
InfusionPoints, LLC provides forecasts, and forward-looking statements, and trends in cybersecurity as directional indicators and not as precise predictions of future events. While our opinions are based on our current judgment based on available information and analysis, they are subject to risks and uncertainties that could cause actual results to differ materially. You are cautioned not to place undue reliance on these forecasts and forward-looking statements, which reflect our opinion as of the date of publication for this document.
Please keep in mind that we are not obligating ourselves to revise or publicly release the results of any revision to these forecasts and forward-looking statements in light of new information or future events.
©2023 InfusionPoints, LLC. Company and product names are used for informational purposes only and may be trademarks of their respective owners.


